By Russ Combs and Jon Munshaw.
We are inching closer to the final release of Snort 3.
Snort 3.0 is an updated version of the SNORT® Intrusion Prevention System that features a new design and a superset of Snort 2.X functionality that results in better efficacy, performance, scalability, usability and extensibility.
There are many benefits of upgrading to Snort 3 once the final release is here. In the coming weeks, we’ll be outlining many of these changes to answer users’ most burning questions and assist everyone in the transition.
Some of the major new features and improvements in Snort 3 include:
- Support for multiple packet processing threads, which frees up more memory for packet processing
- Use of a shared configuration and attribute table
- Access to more than 200 plugins
- Support for Hyperscan, which leads to faster fast patterns, content literals and compatible PCRE during signature evaluation and various searches from inspectors
- Rewritten TCP handling
- New rule parser and rule syntax
- Improved shared object rules, including the ability to add rules for zero-day vulnerabilities
- New performance monitor
- New time and space profiling
- The ability to scale in a simpler way to leverage multiple cores
- The ability to process a raw payload, such as bridging two sockets and performing an inspection
- The ability to pause and resume commands
- New rule remarks and comments that are inside of the rule itself
- And so much more
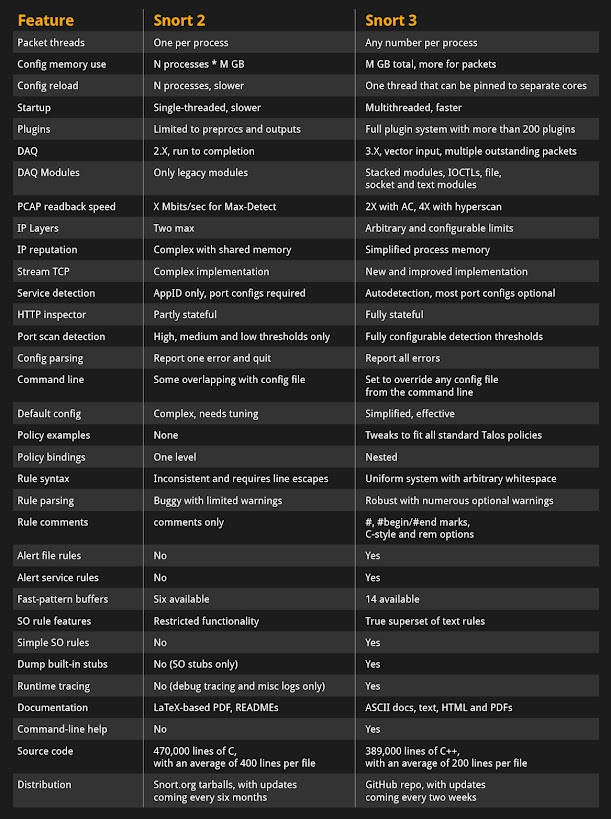
For the die-hard Snort 2 users out there, the table below will break down how the most popular Snort features will stack up in the change from 2 to 3. If you have any questions, please do not hesitate to reach out to any of our mailing lists.
You can subscribe to Talos' newest rule detection functionality for as low as $29 a year with a personal account. Be sure and see our business pricing as well here. Make sure and stay up to date to catch the most emerging threats.